
Many of us would have heard about the scam where a fake e-mail is sent to a user's e-mail account posing as a bank or credit card provider. The number of such e-mails is rising at a shocking rate: so much so, that phishing (as this scam is called) now represents the biggest form of online identity theft.
And even highly educated can fall prey to these scams, in the process losing their money and peace of mind. So what's this all about, and how can you be safe?
What is phishing?
Phishing is an attempt by fraudsters to 'fish' for your banking details. A phishing attempt usually is in the form of an e-mail that appears to be from your bank.
The e-mail usually encourages you to click a link in it that takes you to a fraudulent log-on page designed to capture your details.
E-mail addresses can be obtained from publicly available sources or through randomly generated lists. Therefore, if you receive a fake e-mail that appears to be from a known banking major (SBI, ICICI Bank, HDFC, etc), it does not mean that your e-mail address, name, or any other information has been taken from our systems.

How do fraudsters operate?
Fraudsters send fake e-mails claiming that your information has been compromised, due to which your bank account has been de-activated/suspended, and ask you to hence confirm the authenticity of your information/transactions like credit card number, personal identification number (PIN), passwords or personal information, such as mother's maiden name.
In order to prompt a response, such e-mails usually resort to using statements that convey an urgent or threatening condition concerning your account.
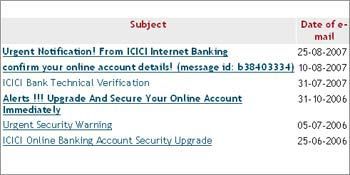
While some e-mails are easy to identify as fraudulent, others may appear to be from a legitimate source.
However, you should not rely on the name or address in the 'From' field alone, as this can be easily duplicated.
Very often, such phishing e-mails may contain spelling mistakes. Even the links to the counterfeit web sites may contain URLs (unique resource locators, or 'links' in simple language) with spelling mistakes, to take you to a fake web site which looks like that of your bank.
Some fake e-mails promise you a prize or a gift certificate if you complete a survey or answer a few questions. In order to collect the alleged prize, you may be asked to provide your personal information.
Fake e-mails appear to be sent by companies to offer a job. These are often for work-at-home positions that are actually schemes that victimise both the job applicant and other customers.
Fake e-mails may direct you to counterfeit web sites carefully designed to look real. Hence, such web sites may look very similar and familiar to you, but are in fact used to collect personal information for illegal use.
Such e-mails attempt to convey a sense of urgency or threat. Example (see image): 'Your account will be closed or temporarily suspended if you don't respond.' Or, 'You'll be charged a fee if you don't respond.'
In its basic form, phishing works by persuading users to give away confidential information -- such as their credit card details or online banking passwords -- on replica bank or credit card provider Web sites.
Since phishing first emerged, these bogus Web sites have become increasingly more sophisticated in the way they mimic the original versions. They are also growing at a rapid rate: according to the Anti-Phishing Working Group, there were 20,109 unique phishing reports received in May 2006, representing an increase by three thousand attacks since April; the worst-ever recorded.

You may be a victim and not even know it!
Earlier versions of phishing e-mails required the recipient to visit what appeared to be their bank or credit card provider's Web site and manually input their passwords.
Now, a new breed of phishing e-mails simply requires the recipient to to a bogus Web site, giving criminals easy access to any confidential passwords and log-in details.
To make matters worse, this is all conducted invisibly, without users ever realising they have been victims of phishing, until they check their financial statements and receive an unpleasant surprise.
This new form of phishing is more likely to be successful as well, since there is no way a user can stop the keylogger application from downloading once they have clicked on the embedded link. It is also a lot easier to access a user's details via this method than by hacking into a bank account and could, potentially, be more lucrative.

How to be safe
1. Avoid unknown Web sites and be suspicious of e-mail messages from any company asking for personal or financial information such as user names and passwords, credit card numbers, and other sensitive personal information.
2. Do not click any links inside an e-mail. Instead, go directly to the valid company's site then log on from there or call the company directly.
3. If you want to find your online bank, always type its URL into your browser.
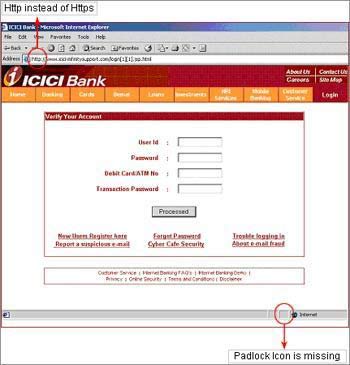
4. Ensure that any Web site visited is secure when submitting sensitive information such as credit card numbers. One indication that a Web address is secure is if it starts with https:// rather than https://. Another indication is a padlock icon at the bottom of the screen, which when clicked, displays a security certificate.
5. Do not open attachments in e-mails unless you are absolutely sure you're waiting to receive that particular file.
6. Ensure that your browser is up-to-date and security patches are always promptly applied. For IE (Internet Explorer) browsers, a special patch relating to certain phishing schemes can be downloaded at microsoft.com securely. You can even consider an alternate browser such as Firefox or Opera, as IE has often been a favourite hacker target.
7. Keep your PC operating system up to date and update your anti-virus software frequently.
8. Use a personal firewall.
9. You can use one of the many available anti-phishing toolbars that can alert you when you encounter a known Phishing Site.
10. You can also get software to detect and remove spyware.
11. Do not use the same password for all of your online accounts.
12. Do not store online account information and passwords in files held on your computer.
13. Knowledge is still extremely important in protection - especially as it has become so difficult to know if an e-mail is valid or not. It is important to educate oneself on Internet fraud. There are several Web sites dedicated to giving free education regarding Internet fraud. The Anti-Phishing Working Group provides information/ reports on the latest Phishing attacks. The Websense Security Labs send out security alerts as and when attacks occur, as does Trend Micro.
Ok, that was phishing. But what in the world is vishing?

What is 'Vishing'?
Vishing is a combination of Voice and Phishing that uses Voice over Internet Protocol (VoIP) technology wherein fraudsters feigning to represent real companies such as banks attempt to trick unsuspecting customers into providing their personal and financial details over the phone.
A typical vishing attack could follow a sequence such as this:
The fraudster sets up an automatic dialler which uses a modem to call all the phone numbers in a region.
When the phone is answered, an automated recording is played to alert the customer that his/her credit card has had illegal activity and that the customer should call the recorded phone number immediately. The phone number is with a caller identifier that makes it appear that they are calling from the financial company they are feigning to represent.
When the customer calls the number, it is answered by a computer-generated voice that tells the customer they have reached 'account verification' and instructs the consumer to enter his/her 16-digit credit card number on the key-pad. A visher may not have any real information about the customer and would address the customer as 'Sir' and 'Madam' and not by name or the prefix 'Mr....' or 'Ms...'.
Once a customer enters his/her credit card number, the 'visher' has all ofthe information necessary to place fraudulent charges on his/her card. Those responding are also asked for the security number found on the rear of the card.
The call can then be used to obtain additional details such as security PIN, expiry date, date of birth, bank account number, etc.
Read on for tips to be safe from vishing

Tips to protect yourself from Vishing
Your bank would have knowledge of some of your personal details. Be suspicious of any caller who appears to be ignorant of basic personal details like first and last name (although it is unsafe to rely on this alone as a sign that the call is legitimate). If you receive such a call, report it to your bank.
Do not call and leave any personal or account details on any telephone system that you are directed to by a telephone message or from a telephone number provided in a phone message, an e-mail or an SMS especially if it is regarding possible security issues with your credit card or bank account.
When a telephone number is given, you should first call the phone number on the back of your credit card or on your bank statement to verify whether the given number actually belongs to the bank.
That's phishing and vishing. So what is skimming?

What is Skimming?
Skimming is a method used by fraudsters to capture your personal or account information from your credit card.
Your card is swiped through the skimmer and the information contained in the magnetic strip on the card is then read into and stored on the skimmer or an attached computer. Skimming is a tactic used predominantly to perpetrate credit-card fraud -- but it is also a tactic that is gaining in popularity among identity thieves.
Check out how skimmers operate. . .

How 'skimmers' operate:
At ATM machines: Fraudsters insert a skimming device to the ATMs card slot. This device scans the card and stores its associated information. While a customer keys in his PIN, the wireless skimming device transfers the data to the fraudsters. This information is then used by the fraudsters for online shopping or to make counterfeit credit cards.
At restaurants/shopping outlets: At restaurants and shopping outlets, the credit card is swiped twice, once for the regular transaction and the other in the skimmer that captures the personal information which is retrieved later by the fraudsters.
Tips to protect yourself from Skimming
Okay, so now what is spoofing?
What is Spoofing?
Web site spoofing is the act of creating a web site, as a hoax, with the intention of performing fraud.
To make spoof sites seem legitimate, phishers use the names, logos, graphics and even code of the actual web site.
They can even fake the URL that appears in the address field at the top of your browser window and the Padlock icon that appears at the bottom right corner.
Fraudsters send e-mails with a link to a spoofed web site asking you to update or confirm account related information.
This is done with the intention of obtaining sensitive account related information like your Internet Banking user ID, password, PIN, credit card / debit card / bank account number, card verification value (CVV) number, etc..
Read on to find out how to be safe from spoofing
Tips to be safe from Spoofed web sites
Banks will never send e-mails that ask for confidential information. If you receive an e-mail requesting your Internet Banking security details like PIN, password or account number, you should not respond.
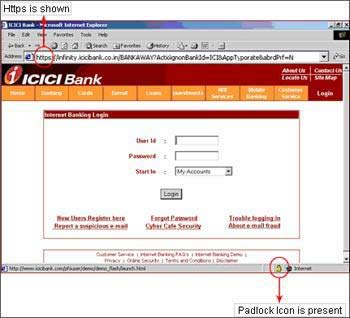
Check for the Padlock icon: There is a de facto standard among web browsers to display a Padlock icon somewhere in the window of the browser For example, Microsoft Internet Explorer displays the lock icon at the bottom right of the browser window. Click (or double-click) on it in your web browser to see details of the site's security.
Check the webpage's URL. When browsing the web, the URLs (web page addresses) begin with the letters 'http'. However, over a secure connection, the address displayed should begin with 'https' - note the 's' at the end.
For example: Our home page address is https://www.icicibank.com. Here the URL begins with 'http' meaning this page is not secure. Click the tab under 'Login'. The URL now begins with 'https', meaning the user name and password typed in will be encrypted before being sent to our server.
But how to find out if an e-mail is genuine?

How to find out if an e-mail is genuine
Finding out whether an e-mail is genuine or not is not very difficult. Every e-mail message contains headers that have the following information:
Origin, which shows information about the machine that sent it,
Relay, which shows the sender machine relaying it to another, and
Final destination, which shows the machine that receives it, the IP address and the domain name.
For example, check out this URL: https://www.lse.ac.uk/itservices/help/e-mailheader.htm for an example of what the different things in an e-mail header mean.
By learning how to identify what the header components are you can distinguish whether an e-mail is genuine or spoofed.
So, a little alterness can go a long way in keeping you safe from the rising incidents of online scams and from scamsters siphoning off money from your bank account.